 Today,i am going to show you how you can get email-id,username and password or any user details you want by using KALI LINUX.
Today,i am going to show you how you can get email-id,username and password or any user details you want by using KALI LINUX.
STEPS FOR SETTING UP YOUR SYSTEM.
- Download Kali Linux from here.
- Extract the contents of Kali Linux iso file which you downloaded in step and copy it to pendrive or instead of pendrive burn the iso file in cd if you want to make a cd of it.
- After copying all contents to pendrive or burning the iso file in cd,reboot you system,press F8 on boot-time and select boot from pendrive if you have copied all the files in pendrive,else boot from cd-rom if you burn the iso file in cd.
- After selecting the boot from device,the kali installation window will open,install accordingly as per your requirement.
- NOTE:During installation,in mount point of selected installation drive,set mount point to "/".
- Remember the username and password while installation as this will be necessity for this hacking method.
- Once,installation is completed,system will reboot,login your account.
- Your system is ready for use.
- Method which we are using to hack the username and password or any user details isSocial Engineering Toolkit method.
NOW LETS SET IT UP.
- Open terminal using ctrl+alt+t or click on the small black window image on the top left of your screen.
- Once terminal is open,type the code carefully.
sudo root
Then enter your root username and password.Don't close the terminal.
- Next step is to open social engineering toolkit.For this type the below command in terminal.
se-toolkit
You will see something in terminal of your system as shown below in the image.

- As shown above in image,you too will see the menu in your terminal.Press "1" and hit enter as we are going to do Social-Engineering Attacks.You will see something in terminal as shown below in the image.
- Once again,you will get a menu as shown above in the image.We are going to select Website Attack Vectors,so press "2" and hit enter.You will see something as shown in the image below.
- In this method,we are going to get the credential of the victim,so press "3" and hit enter as it will select credential harvester attack method.This will open new menu as shown below in the image.
- Since,we want the username and password which is credential of victim,so we need to trap the victim in a look a like page to original website page(like phishing page) and for that we need to clone a website.To do this,press "2" and hit enter which will open something like shown below.
In above image,you might have noticed a red colour rectangle box made by me,in that box,you will find "tabnabbing:XXX.XX.XXX.X" where this "XXX.XX.XXX.X" is you computer IP address.To find IP address of your computer,open a new terminal and type the command given below.
su root
enter_your_root_password
ifconfig
In above command,we first gain the root access,and then afterwards type "
ifconfig" and hit enter to get the
IP address.
Copy paste this
IP address at the end of "
Tabnabbing:".I have used my
IP address but for security reasons i can't reveal it,so i have posted here "
XXX.XX.XXX.X".Please note that,if you
don't put your computer IP address,they this method won't.After entering your
IP address,hit enter.It will ask your to
enter the url of website you want to clone as shown below.Here,i had entered "
www.ymail.com" as i
want to hack someone ymail account.The below image represents all the steps.
It will give a message that its working on cloning the site and will take a little bit time.
Once the process is completed,you will see something as shown in the image below.
- The next step is the most important step,till now we have make your IP address go online and anyone who visit your IP address will see the page which will look like the website of whose url you entered to clone.In this step,you need to shortened your IP address by using services like ADF.LY, Binbox, Goo.gl,etc.Once you enter your ip address on these sites to shorten,they will provide you a link,all you need to do is just send this shortened link to your victim.
- When the victim visit the url which you have sent them,the will see a same page of which url you had entered to clone the website.The victim will think that it is a original page and when the victim enters any of their information,you will see that information in the terminal.
- In this example,i have used ymail.com.Therefore,the victim will see homepage of yahoo mail.This is only the login form,i have entered the login username as:"Kali used to hack email-id and password" andpassword as: "Hacking successfull".

NOTE:VICTIM CAN IDENTIFY THAT THE PAGE IS A TRAP AS THE ADDRESS BAR OF BROWSER WILL BE HAVING YOUR IP ADDRESS.FOR BEST RESULTS,SEND THE SHORTENED URL TO VICTIM MOBILE AND ASK THEM TO VISIT URGENTLY,OR YOU CAN SAY VISIT THIS LINK AND LOGIN TO GET LATEST UPDATES OF THEIR FAVOURITE CONTENTS,ETC.
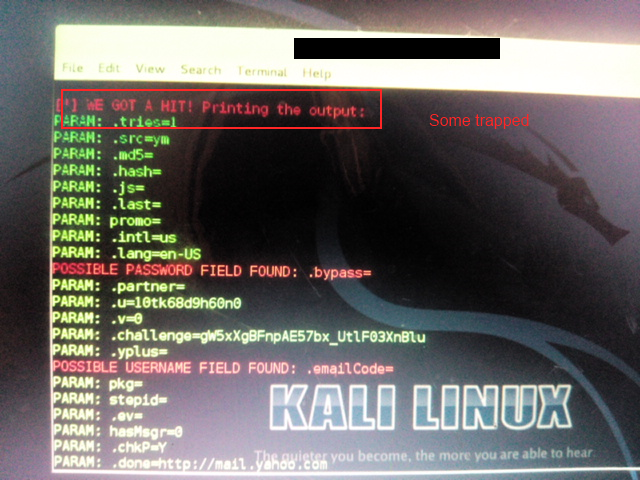
RESULT.
The
username and password will be shown
in terminal window and will be similar to the
image shown
below.
IF YOU GET STUCK ANYWHERE,FEEL FREE TO CONTACT US AND GET SOLUTION FOR YOUR PROBLEM RELATED TO THIS INFORMATION.I WILL SUGGEST YOU TO USE VIRTUAL BOX FOR USINGKALI LINUX WITHIN YOUR DEFAULT OPERATING SYSTEM.VIDEO TUTORIAL WILL BE GIVEN ON DEMAND.SO IF YOU NEED VIDEO TUTORIAL RELATED TO THIS,JUST CONTACT US FROM CONTACT FORM BELOW AT RIGHT CORNER OF THIS PAGE.
PLEASE DON'T FORGET TO SHARE THIS INFORMATION WITH YOUR FRIENDS.
NOTE:ABOVE INFORMATION IS FOR EDUCATION AND SECURITY PURPOSE ONLY.IF YOU MISUSE OR MISTREAT THE ABOVE INFORMATION,THEN IT CAN BRING UNLAWFUL CHARGES BY THE PERSON ON WHOM YOU SET THIS TRAP.THE AUTHOR WILL NOT BE RESPONSIBLE IN THE EVENT ANY UNLAWFUL CHARGES ARE BROUGHT TO YOU BY ANY INDIVIDUALS BY MISUSING THE ABOVE INFORMATION.WE WON'T TAKE RESPONSIBILITY FOR ANY OF YOUR ACTION RELATED TO ABOVE INFORMATION.
 Today,i am going to show you how you can get email-id,username and password or any user details you want by using KALI LINUX.
Today,i am going to show you how you can get email-id,username and password or any user details you want by using KALI LINUX.












Comments